Help identify vulnerabilities that adversaries can exploit, enabling security personnel to remediate and strengthen the IT security posture.

Systematic examination of an information system to determine the adequacy of security measures, identify security deficiencies and areas of improvement.

A cyber risk assessment identifies backdoor in key security controls in applications. It also focuses on preventing application security defects and vulnerabilities.

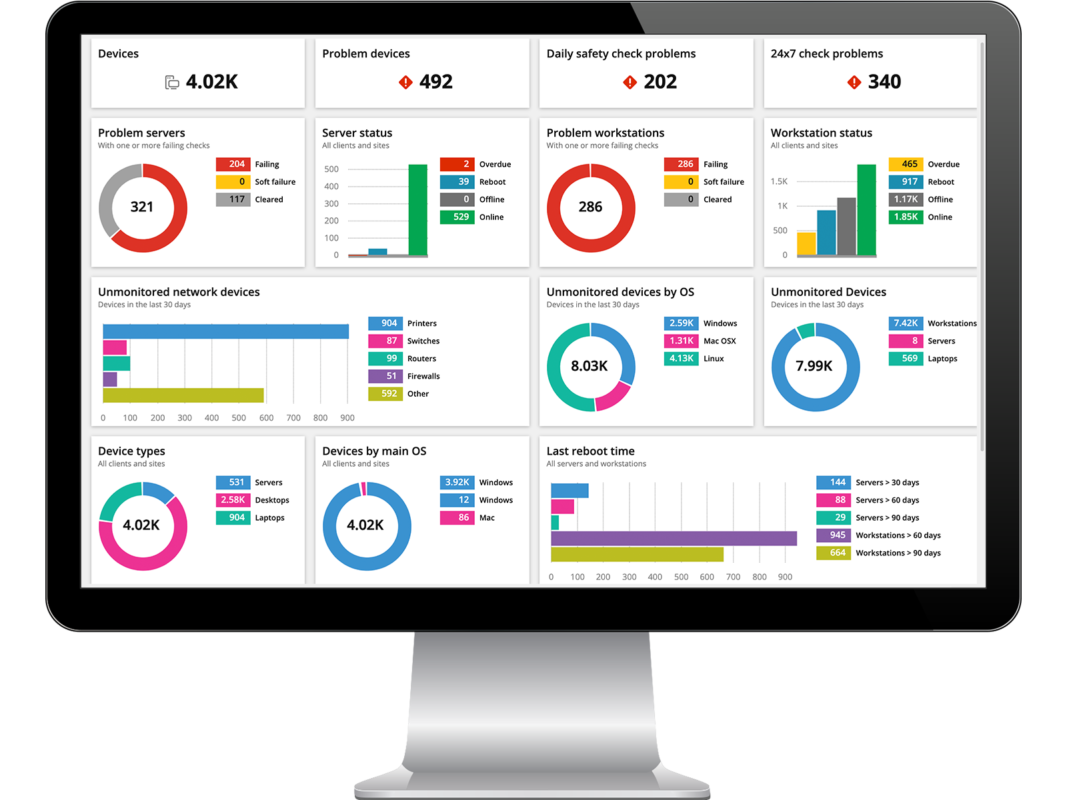
SOC Team detects, prioritizes, investigates, and responds to security threats. It combines threat intelligence, machine learning-based anomaly detection, and rule-based attack detection techniques to detect sophisticated attacks, and incidents are managed effectively and remediating detected threats. Security Operations Centers (SOCs) use various tools to monitor and protect an organization’s networks and systems from cyber threats. Some of the most common tools used in SOCs include:
Intrusion Detection and Prevention Systems (IDPS) — monitor network traffic for signs of malicious activity and can automate actions to block or quarantine suspected threats. Security Information and Event Management (SIEM) Systems — SIEMs collect and analyze log data from various sources, such as network devices, servers, and applications, to identify potential security threats and suspicious activity.
Threat Intelligence Platforms — These platforms gather and analyze intelligence from various sources, such as threat feeds and open-source information, to identify known and emerging threats.